Authentication and Authorization Using OAuth 2.0 Protocol
Sentinel RMS Cloud License Manager provides industry-standard OAuth 2.0 protocol-based authentication and authorization for your users/applications. The following table describes the differences between the support and mechanisms provided for on-premises and SaaS applications:
| Topic | On-premises Applications | SaaS Applications |
|---|---|---|
| Based on OAuth 2.0 |
Resource Owner Password Credential flow |
Client Credentials flow |
| Use Case |
>The licensed application is installed on-premises. >The users/machines must be authenticated for using the RMS Cloud LM REST API. |
>The licensed application is hosted in a trusted environment (private cloud). >Your application needs to be authenticated for using the RMS Cloud LM REST API. |
| Sentinel RMS Licensing Options |
>Unified APIs in the SCP-integrated library
>RMS Cloud LM REST API
|
RMS Cloud LM REST API
|
| Authentication |
>An OAuth access token is required to make requests to Sentinel RMS Cloud License Manager. >The licensed application gets an auth token in exchange of the registration token. An auth token consists of an access token and a refresh token. >Once obtained, the refresh token can be used to obtain a new access token. >The Contact Administrator on the customer's site creates the registration token for users/machines in an enterprise. |
>An OAuth access token is required to make requests to Sentinel RMS Cloud License Manager. >The licensed application gets an access token using OAuth 2.0 Client Credentials flow. The software vendor must provide the application/client credentials for the licensed application. See also: SaaS Applications >These credentials must be kept safe. NOTE The software vendor cannot generate and support multiple application/client credentials. |
| HTTP Header | Registration Token is customer-specific. Hence, no Customer ID is required as explicit input for the licensing calls. | A custom header, x-sntl-customer-id, is required to identify a customer and is passed as the HTTP header. |
| Signing and Verification |
Your application running in a hostile environment must follow the mandatory signing and verification requirement for securing client/server communication. **WARNING** REST API signing is not yet supported in the Sentinel EMS WS Reference tool. Hence, the use of the tool for exploring the registration token workflow and accessing the Cloud LM REST APIs is not recommended. |
No signing/verification is required. |
| Developer Resources |
Contact your Thales representative to obtain a package that contains the: >Postman collections >YAML files |
Use your Sentinel EMS hosted instance for accessing the Sentinel EMS WS Reference tool. |
| Documentation Reference | Getting Started with Sentinel RMS—Connected (Cloud LM) Mode for On-premises Applications | Getting Started with Sentinel RMS— for SaaS Applications.Connected (Cloud LM) Mode |
On-premises Applications
Authentication Workflow for on-premises applications is supported using the:
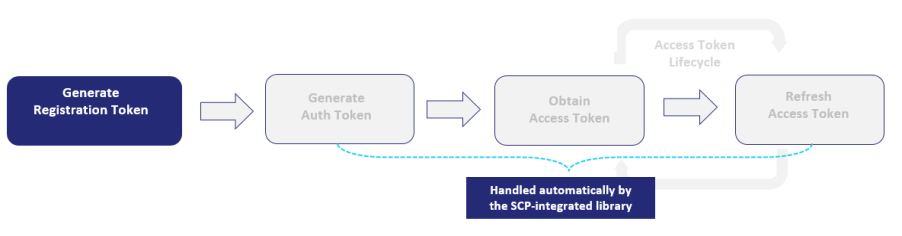
As shown in the diagram above:
>The SCP-integrated library consumes a registration token.
>The SCP-integrated library performs the authentication tasks—such as contacting the Token Management Service REST API, obtaining an auth token, and refreshing an access token. For details, refer to the Getting Started with Sentinel RMS—Connected (Cloud LM) Mode.
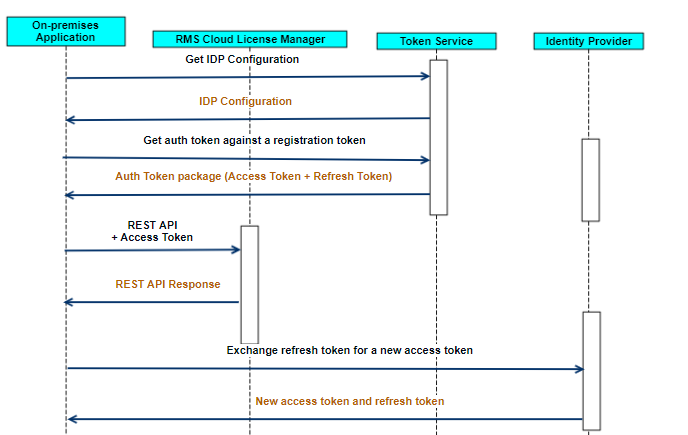
Each Cloud LM REST API, must be authenticated using a JSON Web Token (JWT) access token. The workflow for authenticating users/devices for the REST APIs is depicted below:
SaaS Applications
Each Cloud LM REST API, must be authenticated using a JSON Web Token (JWT) access token. The workflow for authenticating applications is depicted below:

