End-User Keys
Two types of Sentinel protection keys are available:
>The Sentinel HL key is a physical USB or ExpressCard key that connects to a computer, or a chip that is embedded in the computer.
>The Sentinel SL key is a software-based key that locks your software to a specific machine. Your software and the user license are locked to the Sentinel protection key that you select.
Sentinel HL Keys
All Sentinel HL keys—with the exception of Sentinel HL Basic keys—contain internal read/write memory. You can use the memory to do any of the following:
>Control access to specific software modules and/or packages
>Assign a unique code to each software user
>Store licenses from your own licensing schemes
>Save passwords, program code, program variables, and other data
Sentinel HL keys are distributed with your software to end users. The keys connect to the end users’ computers. A variety of Sentinel HL keys are available to suit your requirements. Sentinel HL keys are available in either of two configurations:
>Sentinel HL (HASP configuration) keys: These keys are fully compatible with software that requires the older HASP HL keys.
>Sentinel HL (Driverless configuration) keys: These keys provide several advantages over Sentinel HL (HASP configuration) keys:
•(On a Windows machine) Employ HID drivers instead of HASP key drivers. (HID drivers are an integral part of the Windows operating system.) In many cases, it is possible to use these keys without installing any additional support software.
•(On a Windows machine) Support the use of "AppOnChip" functionality. With AppOnChip, code fragments of selected functions in the protected application are protected from an attacker's eyes by storing them as encrypted data. The code fragments are only decrypted and executed inside the HL key. This provides significantly enhanced security for the application.
•(On a Linux machine) In many cases, it is possible to use these keys without installing any additional support software.
•Support a higher number of Features.
•Provide larger on-key memory space.
•All Driverless keys (except for Basic keys) support a virtual clock for time-based licenses.
•All Driverless keys (except for Basic keys) support concurrency (network-based licenses).
Sentinel HL keys offer the highest level of security. In order for a user to access your software, and for it to function correctly, the key must be accessible by the application. Furthermore, Sentinel LDK uses LicenseOnChip technology to protect Sentinel HL keys against license tampering.
Sentinel HL keys also have the advantage of portability. This means that the key can be moved from one computer to another. Software may therefore be installed on multiple computers but will only run if the key is connected and authenticated by the software.
NOTE A Sentinel HL key can be accessed using a virtual connection. For more information, see Virtual Connection of HL Keys.
Benefits of Sentinel HL Key Protection
Sentinel HL key protection provides the strongest level of protection against piracy. The correct functionality of the software depends on the internal logic of the Sentinel HL key, which is virtually tamper-proof.
In addition, Sentinel HL key protection:
>Offers the strongest enforcement for license terms, which are stored and protected inside the Sentinel HL key.
>Enables portability—the software can be used on any computer to which the Sentinel HL key is connected.
>Does not require transaction with the software vendor to enable activation of the Product.
Maximum Number of Features in a Sentinel HL Key
While the number of Features that can be written to a Sentinel SL key is unlimited, each Sentinel HL key can contain a certain maximum number of Features, depending on:
>the type of HL key
>the number of Products among which the Features are distributed
>the complexity of the license model defined in each Feature:
•Lowest complexity: Perpetual HL
•Medium complexity: Perpetual HL + SL, Expiration Date
•Highest Complexity: Execution Count,
For example, a Sentinel HL Max (Driverless configuration) key can contain:
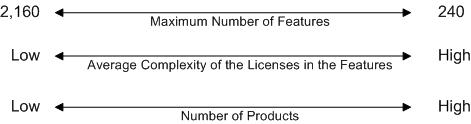
This diagram illustrates that:
>As you increase the number of higher-complexity license models on the key, the maximum number of Features that the key can contain decreases.
>As you increase the number of Products on the key, the maximum number of Features that the key can contain decreases.
For information on the range of Features that each Sentinel HL key can contain, see the Sentinel HL Data Sheet.
NOTE In Sentinel HL (Driverless configuration) keys, Features are stored in dynamic memory space. This space is shared between application data (the space available to you for your applications) and Features. All space that is not utilized for Features can be used for application data. For more information, see Defining Protection Key Memory Data.
Sentinel SL Keys
Sentinel SL keys are virtual, software-based keys that reside in the secure storage of a specific computer. Sentinel SL keys provide the same functionality as Sentinel HL keys, without requiring physical distribution.
The following types of Sentinel SL keys exist:
>SL AdminMode - SL keys that provide the highest level of security and functionality
>SL UserMode - SL keys that provide a greater level of flexibility under certain circumstances
Benefits of Sentinel SL Key Protection
With Sentinel SL key protection:
>Product activation:
•Product activation is instantaneous. End users can immediately start using the software with its fully-licensed functionality.
•The activation process for end users is convenient and transparent.
•The online connection with end users can enable user registration data to be collected and used for marketing purposes.
>When using a network license that is locked to a Sentinel SL key, you can specify that a license can be detached from the pool of network seats and attached to a remote recipient machine.
Sentinel SL Unlocked Licenses
An unlocked license is one that is not locked to a specific machine. An application with an unlocked license (referred to as an Unlocked Product) is protected against disassembly. However, the protected application can be duplicated, installed, and used on any machine for as long as the unlocked license allows. Unlocked licenses are used in the following situations:
>Trialware products
The ability to create and distribute trialware products without exposing the protected software to piracy provides a significant marketing advantage when selling software applications. Potential customers can work with the actual application and experience what the application has to offer and how it can benefit the individual or the organization. In addition, anybody that has access to trialware can copy it and distribute it to other people; this multiplies the exposure of the application within the marketplace. Each person who installs and works with the application must, at the end of the grace period (typically 30 to 90 days), decide to purchase an HL or SL key for the application or else be blocked from using the application.
>Unlocked products
Unlocked products are used when vendors want to protect their applications against reverse engineering but either:
• Have no need to license the application (for example, software that is part of a larger hardware package). The vendor may not need to protect against duplication of the software. However, they want to protect the software against theft of intellectual property.
• Are using a separate product or system to handle licensing of the software.
An unlocked product typically has no time restriction or has a long-term license.
