Basic Protection Workflow
This section provides a workflow that describes the elements of protecting applications using Sentinel LDK Envelope. Additional information about specific procedures is provided in the Sentinel LDK Envelope for Windows.
1.Launch Sentinel LDK Envelope from Sentinel LDK Launcher.
2.Add the executable, library, or .NET assembly you want to protect to the project.
3.Define protection parameters for the protected application.
4.Protect the program.
5.Distribute the protected software together with your encrypted Sentinel protection keys.
NOTE Sentinel LDK Envelope does not affect the files being protected. However, it is highly recommended that you designate a separate output folder for the protected application in order to distinguish between source (unprotected) and output (protected) files.
Sentinel LDK Envelope protection involves the application of protection parameters that are controlled by the engines running Sentinel LDK Envelope. You apply these parameters to an unprotected source.
Sentinel LDK Envelope does not affect the original files or the way a protected application actually works. The only modification is that user access is conditional on the presence of a required Sentinel protection key. If the Sentinel protection key is present, the protected file runs.
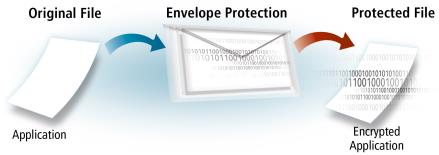
The logic of Sentinel LDK Envelope protection is illustrated in the following diagram. Note that the original file can be a Win32, or Windows x64 executable or DLL; a Windows .NET assembly executable or dynamic library; a Java executable; a Linux executable or shared object; or a Mac binary.
To ensure the highest level of security for your software, Sentinel LDK Envelope for Win32 removes debugging data from the programs that it is protecting.
It is recommended that Linux software engineers strip extraneous symbols from the executable prior to protecting with Sentinel LDK Envelope.
