Creating a Product
When you define a Sentinel LDK Product, you can specify the following:
> The Features the Product contains
> The protection level for the Product, including clone protection schemes for Sentinel SL-type keys
>Individual license terms
>The content and layout of the memory data stored in Sentinel protection keys
NOTE For details on creating a product with an SL license that can be used while detached from the network (offline), see Working with Detachable Licenses.
To create a Sentinel LDK Product:
1.
Open the Create New Product page![]() Show me how
Show me how
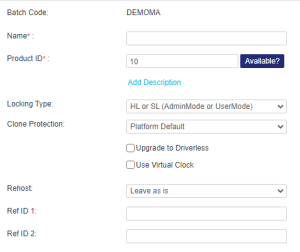
2.Define the product as follows:
| Option | Description |
|---|---|
| Name |
Enter a name for the product. Value: >Maximum 50 characters. >Must be unique in the batch. >Case-insensitive (for example, Trial, TRIAL, and trial are considered identical. |
| Product ID |
Accept the automatically generated, sequential Product ID or assign your own numeric identifier. For example, you may want to maintain consistency with existing Product data. Value: >Between 2 and 65471. >Must be unique in the batch. |
| Add Description |
(Optional) Add a description to the Product. Maximum: 510 characters |
| Locking Type |
Select the locking type for the Product based on the type of protection key to be distributed and the required level of security and functionality: About Sentinel Protection Keys: >Sentinel HL keys provide hardware-based protection by connecting a physical unit, such as a USB device, Express Card, or chip, to the customer's machine. >Sentinel SL keys are virtual, software-based keys that reside in the secure storage of the customer's machine. Although SL keys provide a high level of protection, HL key security is superior. If the locking type allows for both HL and SL keys, then HL key-level protection is provided if the Product is shipped only with HL keys (that is, the Product is never shipped with SL keys). If the Product is shipped with SL keys, then the overall level of security should be considered to be that provided by SL keys. This is because there is always the possibility that an attacker might have access to a deployed SL key. For more information, see the section on choosing the protection level for your Products in the Sentinel LDK Software Protection and Licensing Guide. |
|
The clone protection scheme to apply to Products with Features. >Platform Default: Uses the clone protection schemes for the Default Clone Protection Version version selected in the License Security Settings section of the Administration Console. >Advanced: Lets you specify pre-defined or custom clone protection schemes for physical and virtual machines. For details, see Advanced Clone Protection Options. Relevant for: SL locking type only because software that is protected by a Sentinel HL key is not vulnerable to machine cloning |
|
| Upgrade to Driverless |
See Upgrading Sentinel HL keys to Driverless Configuration for details. Relevant for: HL locking type only |
| Use Virtual Clock |
Lets you manage time-based licenses for Sentinel HL (Driverless configuration) keys using a virtual clock when no real-time clock is available. NOTE For Products that are licensed with Sentinel SL keys, Sentinel HL Time keys, and Sentinel HL NetTime keys, V-Clock is always available. For details, see Enabling V-Clock for Sentinel HL (Driverless Configuration) Keys. Relevant for: HL locking type only |
|
Rehost |
If you selected the one of the SL locking types, in the list, select one of the following: >Enable. Enables rehosting for the Product. >Disable. Disables rehosting for the Product. >Leave as is. Uses the rehosting value in the Protection key. >Specify at entitlement time. Uses the rehosting value specified when generating the Entitlement. Relevant for: SL locking type only |
|
Ref ID 1 Ref ID 2 |
(Optional) Enter information that identifies the Product in a different system, for example, a Product code in your company's ERP system. Value: Maximum 250 characters |
3.(Optional) Add Features to the Product and define their license terms. (You can perform this step later, if needed. Clone protection is available only for Products with Features.)
•Add Features to the Product, as needed:
a.Click Add Features. The Add Features to Product dialog box opens.
b. Select the Features to add, and click Add Features to Product. The associated Features are displayed in the Product Features tab.
c.For each Feature, select one of the following to specify if the Feature can be excluded or is always included when generating an Entitlement:
| Can be excluded | Enables the order taker to remove the Feature from the Product when generating an Entitlement, as needed. |
| Always included | Ensures that the Feature is always included in the product when generating an Entitlement. |
| All | Sets all Product Features in the list to Can be excluded. |
| None | Sets all Product Features in the list to Always included. |
•Configure the license terms, if needed. For details, see Defining License Terms for a Sentinel LDK Product.
| To configure the license terms for a single feature | Click Configure. |
| To configure the license terms for multiple features simultaneously | Select the relevant check boxes and click Configure Selected. |
| To remove a Feature from the Product | Click Remove. |
| To remove multiple Features from the Product | Select the relevant check boxes and click Remove Selected. |
NOTE You cannot modify the Locking Type after associating Features. To change the locking type, first remove all associated Features. Afterward, re-associate the Features with the Product.
4.(Optional) Select the Memory tab to define memory areas and write data for secure storage. For details, see Managing Default and Dynamic Memory Data.
5.When you finish defining the Product details, save the Product:
| To save the Product as a Draft | Click Save as Draft. |
| To save the Product as Complete | Click Save as Complete. |
The new Product is displayed in the Products page.
Advanced Clone Protection Options
If you selected one of the SL locking types, in Clone Protection, you specify the clone protection scheme to apply to Products with Features.
This section describes the Advanced options, which let you specify pre-defined or custom clone protection schemes for physical and virtual machines. For Platform Default clone protection, see above.
Physical Machine
Select a pre-defined or custom clone protection scheme from the following:
| Option | Description |
|---|---|
|
PMType1 |
Verifies fingerprints using the hard drive serial number and motherboard ID. Supported operating systems: Windows, Linux, and Macintosh |
|
PMType2 |
Verifies fingerprints using various criteria, such as CPU, Ethernet card, optical drive, and PCI card slot peripherals, as well as the hard drive serial number and motherboard ID. This scheme provides enhanced reliability against false positive clone detection and maintains the inherent security of the scheme. |
|
PMType3 |
Verifies fingerprints using the CPU model, CPU serial number, and internal storage serial number. NOTE Selecting PMType3 disables clone protection for virtual machines and sets the value of Rehost to Leave as is. |
|
PMType4 |
Verifies fingerprints using the CPU model, CPU serial number, internal storage serial number, Android serial number, and Android Firstboot. This scheme allows users to reinstall licenses on Android without the need for reactivation, provided that features are licensed using Perpetual or Expiration Date licenses. NOTE Selecting PMType4 disables clone protection for virtual machines and sets the value of Rehost to Leave as is by default. |
|
FQDN |
Verifies fingerprints using the machine’s FQDN (Fully Qualified Domain Name). |
|
No Clone Protection |
Disables clone protection for this product on physical machines. NOTE Removing clone protection support critically reduces security for the product. |
|
Opens a list of criteria that you can use to specify your custom-defined clone protection scheme. This is useful, for example, if none of the existing clone protection schemes meet your Product needs. To create a custom scheme: 1.In Custom Scheme Name, enter a unique name for the clone protection scheme (maximum 18 alphanumeric and Unicode characters). We recommend entering a descriptive name that clearly indicates the purpose of the custom scheme. 2.Select one or more required criteria: •CPU—CPU information. Excludes the CPU UID •Ethernet Address—MAC address •FQDN—Fully Qualified Domain Name. Not supported for Android •Hard Disk—Hard disk ID (on a PC) or SD Card ID (on an Android device) •IP Address—IP address •Machine ID—Motherboard (on a PC) or Android device serial number (or Android first boot if serial number is not available) •Security Identifier (SID)—Microsoft Windows Security Identifier (Windows machine only) 3.In Minimum Required Criteria, enter a number between 1 and the number of selected criteria. This specifies the number of criteria that must match when validating the license. For example, if you selected three criteria, enter a number from 1 to 3. 4.To validate the license using all of the selected criteria that are present when a license is generated, select All identifiers present at license generation must exist and match at runtime. For example, suppose the Minimum Required Criteria in your custom clone protection scheme requires 4 out of 5 criteria in the fingerprint. If this option is selected, and all 5 of the criteria are present when the license is generated, then all 5 of the criteria must match the fingerprint at runtime, even though the custom clone protection scheme requires only 4. 5.Click Save. The custom clone protection scheme is applied to the product. The scheme is also added to the list of custom clone protection schemes and is now available for any product in any batch code present in the Sentinel LDK-EMS database. 6.(Optional) Repeat these steps to create additional custom clone protection schemes for use with any product in any batch code present in the Sentinel LDK-EMS database. After you finish creating the required schemes, make sure to select the relevant scheme for the current product and click Save. This applies the selected custom clone protection scheme to the current Product. |
Virtual Machine
Select a pre-defined or custom clone protection scheme from the following:
| Option | Description |
|---|---|
|
VMType1 |
Verifies fingerprints using the Virtual MAC address, CPU characteristics, and UUID of the virtual image. For more details, see the section on clone detection for virtual machines in the Sentinel LDK Software Protection and Licensing Guide. |
| VMType2 |
Provides VMType1 clone protection and accesses the VM Generation ID (if available) to prevent misuse of a VM snapshot. >VMware Player, Workstation, and ESXi. >Hyper-V Server |
|
VMType3 |
Ensures that a protected application in a virtualized server environment cannot be used if the license is copied from one virtual machine to another. Supported virtualization platform: Microsoft Azure Available for: >SL-AdminMode and SL-UserMode on Windows >SL-AdminMode on Linux |
| VMType4 |
This scheme is intended primarily for Docker containers but is also compatible with other virtual machines. This scheme checks the Virtual MAC address, CPU characteristics, UUID, and the hard drive serial number. The values for these characteristics must match in the reference fingerprint and the system fingerprint. If there is any mismatch, the protected application is disabled. For more details on protecting applications in Docker Containers, see the appendix in the Sentinel LDK Software Protection and Licensing Guide. |
|
FQDN |
Verifies fingerprints using the machine’s FQDN (Fully Qualified Domain Name). This scheme provides increased reliability and provides flexibility of operation in a server virtualization environment. |
|
No Clone Protection |
Disables clone protection for this product on virtual machines. NOTE Removing clone protection support critically reduces security for the product. |
|
Opens a list of criteria that you can use to specify your custom-defined clone protection scheme. This is useful, for example, if none of the existing clone protection schemes meet your Product needs. 1.In Custom Scheme Name, enter a unique name for the clone protection scheme (maximum 18 alphanumeric and Unicode characters). We recommend entering a descriptive name that clearly indicates the purpose of the custom scheme. 2.Select one or more required criteria: •CPU—CPU information •Ethernet Address—MAC address •FQDN—Fully Qualified Domain Name •IP Address—IP address •Machine ID—Motherboard (on a PC) or Android device serial number (or Android first boot if serial number is not available) •Security Identifier (SID)—Windows machine only •VM Generation ID—Attribute of a Windows VM that helps to prevent misuse of a VM snapshot 3.In Minimum Required Criteria, enter a number between 1 and the number of selected criteria. This specifies the number of criteria that must match when validating the license. For example, if you selected three criteria, enter a number from 1 to 3. 4.To validate the license using all of the criteria that are present when a license is generated, select All identifiers present at license generation must exist and match at runtime. For example, suppose the Minimum Required Criteria in your custom clone protection scheme requires 4 out of 5 criteria in the fingerprint. If this option is selected, and all 5 of the criteria are present when the license is generated, then all 5 of the criteria must match the fingerprint at runtime, even though the custom clone protection scheme requires only 4. 5.Click Save. The custom clone protection scheme is applied to the product. The scheme is also added to the list of custom clone protection schemes and is now available for any product in any batch code present in the Sentinel LDK-EMS database. 6.(Optional) Repeat these steps to create additional custom clone protection schemes for use with any product in any batch code present in the Sentinel LDK-EMS database. After you finish creating the required schemes, make sure to select the relevant scheme for the current product and click Save. This applies the selected custom clone protection scheme to the current Product. |
For more details, see:
>The section on how Sentinel LDK detects machine cloning in the Sentinel LDK Software Protection and Licensing Guide, which provides a detailed description of each clone protection scheme.