Tracking Usage in Isolated Networks
From Sentinel RMS v9.7 onwards, under the on-premises deployment mode implementation, usage tracking and report generation (via Sentinel EMS) is supported. These reports can be used for analytics and billing purposes of your software. To learn more about the usage data support in Sentinel EMS and Sentinel RMS, refer to the section Software Usage Data of the Sentinel EMS and Sentinel RMS Solution Guide.
The chapter provides the workflow for implementing usage tracking for Sentinel RMS licensed applications running in isolated networks that do not have access to the Internet for transmitting usage data.
In this chapter, the following topics are discussed:
•Settings in the Flexible License Model of Sentinel EMS
•Guiding About Installing and Configuring the SCP Service
•Guiding About Location of Usage Files and their Processing
•Guiding About Permissions for Usage Creation
•Guiding About Location of Acknowledgment Files and their Processing
>Deleting Processed Usage Data on Source Machine
Overview
The machines that are running Sentinel RMS licensed applications (standalone systems or clients of the RMS License Manager) may operate in isolated networks deployed On-premises. The offline usage data continues to be collected on the standalone system or the RMS License Manager host—both referred to as source machines. In both cases, (from Sentinel RMS v9.7 onwards) a single running usage file is used to collect and store usage data.
The usage data is stored in usage files which have a .udb extension. The maximum size of a usage file can be 5 MB.
The system administrator on the end user site carries out transmission of usage data to facilitate generation of reports for such isolated users. The raw data is processed by Sentinel Cloud Connect (SCC) using predefined business rules which aggregates the data. The aggregated usage data is stored in the SCC database. Sentinel EMS queries the aggregated usage data for generating reports and other purposes. The following image describes the complete workflow for managing usage data and generating reports in isolated networks.
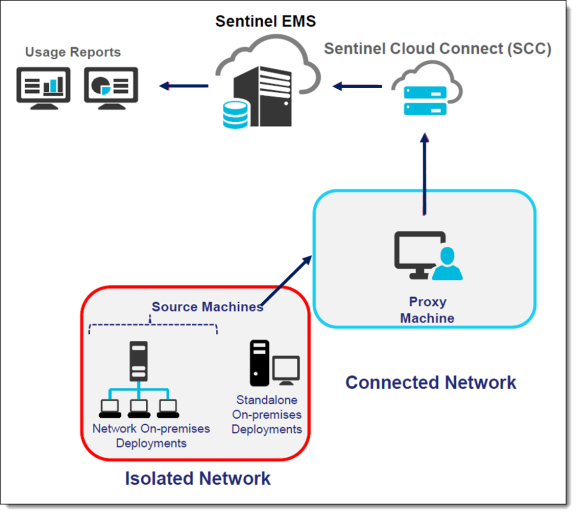
The system administrator needs to copy the offline usage data from the source machine(s) to a storage device. The data from the storage device is then copied to another machine that has Internet connectivity, referred to as the proxy machine. The Sentinel Cloud Plug-in (SCP) service is configured to run (offline mode) on the proxy machine. Using this, data is uploaded to the SCL (Sentinel Cloud Licensing) server. This uploaded usage data is used to generate reports in Sentinel EMS. On the proxy machine, corresponding to the uploaded usage data, acknowledgment data is created. The system administrator further needs to copy the acknowledgment data back to the source machine to ensure that the uploaded usage data is not accumulated over time. The following image provides the sequence of steps performed by the system administrator for copying usage and acknowledgment data between source and proxy machine, respectively.
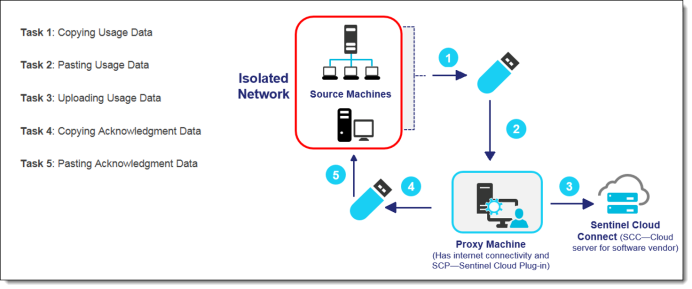
For details about these steps, refer to Usage Data of Isolated Networks in the Sentinel RMS System Administrator Guide.
Usage Tracking Prerequisites
To allow usage tracking in isolated networks, you must meet the following requirements:
>Sentinel Cloud Licensing (SCL) Add-on package
The Sentinel Cloud Licensing (SCL) Add-on package contains the Sentinel Cloud Plug-in (SCP) for various supported platforms. SCP has to be configured on the proxy machine (offline mode) to upload usage data. Contact your designated sales representative in order to obtain the Sentinel Cloud Licensing (SCL) Add-on package in addition to the Sentinel RMS SDK v9.7. Also, refer to the Sentinel Cloud Licensing (SCL) Add-on Installation and Configuration Guide to learn more about the supported platforms.
>Flexible License Model in Sentinel EMS
You need to use the Flexible License Model available in Sentinel EMS for implementing licensing. The usage tracking for isolated networks feature is not supported with any other license model template provided in Sentinel EMS for the On-premises deployment mode (such as Network Node Locked, Standalone Node Locked and so on).
NOTE Specify a customer name at the time of enabling the Collect Usage flag for license activation using the On-premises deployment mode.
Settings and Configuration
You need to ensure all the following points:
Settings in the Flexible License Model of Sentinel EMS
In Sentinel RMS, on the Edit License Model - Flexible License Model page, select the following options to allow usage logging for On-premises deployment mode, along with other settings:
>Under Define Attributes, from the Deployment Type drop-down list, select On-premise Served.
>Under Policy, from the License Version drop-down list, select 21 - RMS 9.7 - <RMS SDK Version>. Here <RMS SDK Version> represent releases later than v9.7 of . Selecting a license version earlier than 21 - RMS 9.7 - <RMS SDK Version>, will not show the usage support settings.
>Under Usage, for Collect Usage, select Yes.
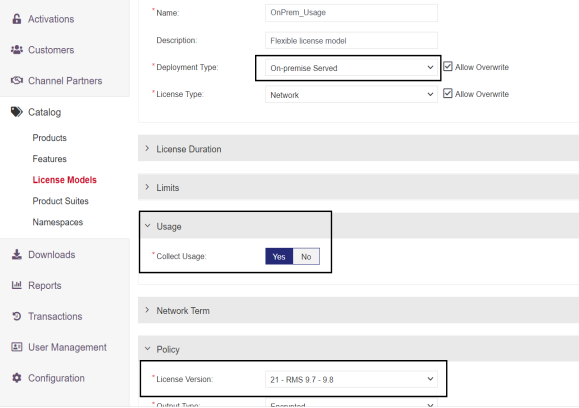
NOTE For standalone licenses, prior to usage generation, ensure that the system is initialized using the sntl_persistence_create API.
Guiding About Installing and Configuring the SCP Service
The SCP service is configured to run in offline mode on the proxy machine in order to pass on the usage data for report generation. The SCP service redistributable and its configuration file (sntlcloudp_configuration_[vendor_alias].xml) is included in the Sentinel Cloud Licensing (SCL) Add-on package.
Follow the information provided in the Sentinel Cloud Licensing (SCL) Add-on Installation and Configuration Guide for details about installing and configuring this service and editing the SCP configuration file. The SCP service is supported on various versions of Windows and Linux. You need to guide the system administrator about accessing and using the information.
Guiding About Ready Usage Files Present on the Source Machine for Upload
The system administrator has to be guided about preparing the usage data present on the source machine for upload. The software vendor must provide a way using the readyUsageForUpload action of the sntl_licensing_transfer API for marking the running usage files as completed. This option is used by the system administrator to prepare the usage for upload before they can start copying usage data to the proxy machine.
For more information on using this API, refer to the sample sntl_tool or the Common Use Case section given in the Sentinel RMS API Reference Guide.
Guiding About Location of Usage Files and Their Processing
The system administrator has to be guided about the location of the usage files on the source and proxy machines, respectively.
In Sentinel RMS v9.7, the usageInfo query (sntl_licensing_get_info) API is introduced. For more information on using this API, refer to the sample sntl_tool or the Common Use Case section given in the Sentinel RMS API Reference Guide.
On the source machine, when the usageInfo API is run, it provides the following two paths:
>The source machine path where the usage data is located.
>The source machine path where the acknowledgment data needs to be copied back after obtaining it from the proxy machine.
As a developer, you have to integrate the usageInfo API with the client application.
The system administrator copies the usage data from the source machine to a storage device. This data is further copied from the storage device to the designated location on the proxy machine. Usage data is processed by the SCP service (offline mode) running on the proxy machine.
Guiding About Permissions for Usage Creation
Starting version 10.2, usage data for lease and on-premises deployment modes on non-Windows can now also be created for non-root, non-group (other) users. Prior to this release, this creation was limited to root and group users only. If desired, you can restrict usage creation permissions. For more information, see Knowledge Base article KB0028071 in the Sentinel Customer Support Portal.
Guiding About Location of Acknowledgment Files and Their Processing
The system administrator needs to be guided about the location of the acknowledgment files on the source and proxy machines, respectively.
The acknowledgment files that are generated on the proxy machine are copied back to the source machine by the system administrator. For each usage file processed by SCP, a corresponding acknowledgment file with the same name (extension .ack) is created.
Locations
On the proxy machine, the Usage, UsageAck, and Corrupted directories are created by the SCP service installation. You need not create persistence data separately.
Base Path
>Windows: C:\ProgramData\SafeNet Sentinel\Sentinel RMS Development Kit\System
>UNIX: /var/slmdata
>Android: /sdcard/slmdata
>Linux ARM: /var/slmdata
1 Proxy machine is supported on Windows and Linux OS.
2,3 Proxy machine is not supported on Android and Linux ARM Operating systems.
>The Usage directory (source machine) contains usage data that is copied from source to proxy machine.
>The UsageAck directory (proxy machine) contains acknowledgment data that is copied from proxy to source machine.
>If usage data is not successfully uploaded, then it is moved to the Corrupted directory.
