Troubleshooting and FAQs
>About Standalone, Network, and Integrated Libraries
>About System Initialization, Persistence, and Cleaning
About Deployment Modes
Question: Is the Connected mode different from the Connected (Cloud LM) mode?
Connected mode, introduced in the Sentinel RMS v9.0, is a deployment mode useful for licensing applications that are hosted in the cloud or are always connected to the cloud. However, implementation of the Connected mode is different from all other deployment modes as:
>The entitlements to support the Connected mode are created using the Connected License Model in Sentinel EMS. Whereas, the entitlements to support all other deployment modes—Connected (Cloud LM), Lease, and On-premises mode—can be created using the Flexible License Model.
>Unlike all other deployment modes, Connected mode does not use the Unified APIs contained in the SCP-integrated library for implementation. Instead, it uses Java and .NET-based licensing libraries and Web services contained in the SCL Add-on package.
With the introduction of the Connected (Cloud LM) deployment mode, the Connected mode continues to be supported. Nevertheless, you should consider using the Connected (Cloud LM) mode for new implementations.
Quick Comparison of Connected mode and Connected (Cloud LM) Mode
| Criteria | Connected Mode | Connected (Cloud LM) Mode |
|---|---|---|
| Introduced in | SCL Add-On v9.0 | SCL Add-On v10.0 |
| License Model in Sentinel EMS | Connected License Model |
Flexible License Model (The same license model is used for the Lease and On-premises modes) |
| License Manager |
Sentinel Cloud Connect, hosted and managed by Thales |
Sentinel Cloud LM (License Manager), hosted and managed by Thales |
| Licensing API | A variant of Unified API that does not map with the Lease mode and On-premises mode Unified API. | A compact set of Unified API that is consistent with the Lease mode and On-premises mode. |
| Language Interfaces |
>Sentinel Cloud Connect web services >Java >.NET |
>Unified APIs for: • C •Java •.NET |
| Authentication Mechanism | The Sentinel Cloud Connect web services use the method of Message Signing for authenticating request-response. | OAuth 2.0 protocol-based authentication and authorization for your users/applications and service accounts. |
| Out-of-the-box licensing attributes or schemes supported | ||

|

|
|

|

Same as the 'User Limit' option of Flexible License Model. |
|

|

Same as the 'No Sharing' option of Flexible License Model. |
|

|
Same as the User Name-based sharing, when combined with Unlimited sharing limit under Flexible License Model. |
|

|

|
|

|

|
|

|

|
|
| Usage Collection and Reports |

|

|
| Vendor Information |

|

|
Standalone, Network, and Integrated Libraries
Question: Do I need to code differently for standalone, network, and integrated environments?
The functions not supported in the standalone client library are actually present but do not perform any meaningful action. Such functions which have no relevance in standalone licensing will return the SNTL_NOT_SUPPORTED_IN_NONET_MODE status code. Similarly, functions which have no relevance in network licensing will return the SNTL_NOT_SUPPORTED_IN_NET_ONLY_MODE status code. The developer can use these as information codes and perform the requisite handling in the code. Hence, you do not need to make any source code changes when moving from a network client library to a standalone client library.
Question: Can LSHOST file/environment variable be used to set multiple License Manager hosts?
Multiple host names can be defined in the LSHOST environment variable separated by a ~ (tilde) symbol.
Feature Planning
Question: Multiple standalone applications are using the same license store (license file) simultaneously on a customer's system (Linux or Mac). However, not all the licenses are being loaded. How to resolve this?
Before v10.2, if multiple standalone applications used the same license store simultaneously, then some applications failed to load licenses, thus not work properly. Starting 10.2, all the applications will load all the licenses from the same license store using the following information.
You need to incorporate getinfo API's lastStatusInfo query (for C and Java) after the first app_context_new call (for C and Java) in which standalone library initialization takes place. If its status is 210265 (SNTL_LICENSE_RESOURCE_LOCKED), this means there is a failure in loading some of the licenses because of write/delete operations on the license store by another application. In this case, you need to re-initialize the library by first deleting the appcontext, performing cleanup, and then re-creating the appcontext. Repeat these steps until the status of lastStatusInfo is successful.
If the contact License Manager is not set in the application, standalone library initialization does not happen in app_context_new, then this error 210265 can come in the next API when library initialization takes place.
Note that a mix of multiple applications using the older licensing library (prior to v10.2) and new (starting v10.2) using the same license store simultaneously might fail to load all the licenses and it is not recommended.
Question: I want to license multiple features of my application. However, I want to control them with just one license. Is it possible?
Yes. You can create a multi-feature license that will allow you to control up to 63 features via a single license string. However, the license generated will be in short-numeric format.
License Locking
Question: Are the locking codes unique?
The locking codes are not unique in strict sense. However, with effective combinations, the possibility of having same locking codes is rare.
Question: Why do we have two locking criteria related to the disk (Disk ID and Hard disk serial)? Which one should be used?
On Windows, Disk ID is the value derived from Volume Serial Number (VSN) and is assigned by the operating system. When the OS is upgraded or reinstalled, this value can change. For non-Windows operating systems, Disk ID is derived from system directories and their I-Node values. Hard disk serial is the value derived from the hard drive serial number. This value is assigned by the hard drive manufacturer. It does not change when the OS is upgraded or reinstalled.
Before deciding between these two options, you must think of availability vs integrity of the locking information. Disk ID is a weak locking criteria but it is available on all machines (including virtual machines); whereas hard disk serial has high integrity but may not be available on all machines. For client-server locking, hard disk serial should be preferred over Disk ID because hard disk serial does not change with software changes. In case of local locking, Disk ID can be used because local locking is valid for short term license models and availability plays a higher role than integrity of the locking information.
Question: Why are most of the lock selectors disabled in Wechoid?
The Wechoid only enables the available and applicable lock selectors on a system.
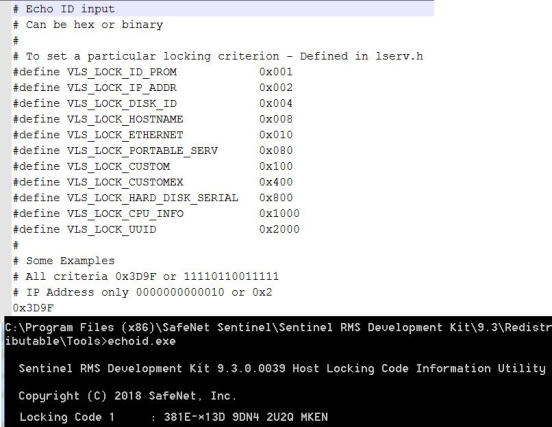
Question: How can I specify primary and secondary locking options in echoid?
You do this by placing two numeric values in the echoid.dat file. Therefore, when the customer uses echoid, the customer will see two locking codes displayed. When you use the license code generator, you know that the first value given by the customer is based on the primary fingerprint, and the second value is based on the secondary fingerprint. See an example below in the screen-shot:
Question: What impact will the following have on the locking code:
>DNS
>DHCP
>Disk formatting
>RAID server
In the case of DNS, DHCP, and disk formatting, the locking values may change and thus there is high risk of failure. In the case of RAID server, you may obtain incorrect values when hard disk serial number (0x800) is used as a locking criteria. To safeguard from this, you can use the standard custom or extended custom lock selectors under such environments.
Question: When should I attach the CID key to the port (USB or parallel) on a system?
In general, the CID key must be attached throughout the application execution. Specifically, for network licenses, the CID key must be attached at the time of loading licenses (when the License Manager is started up and licenses are added dynamically). For standalone licenses, the key must be attached when licenses are requested.
Question: The echoid –d option displays the locking information of the various Ethernet cards installed on a system. However, the sequence followed to enumerate the Ethernet cards is not known?
The locking information for multiple Ethernet cards shown by:
>The echoid utility with –d option.
>Unified API: The SNTL_QUERY_FINGERPRINT_INFO query type of the sntl_licensing_get_info API.
>Traditional API: The VLSgetNumberedMachineID API.
The locking information is arranged in the same order as shown in the Windows registry. However, the sequence may differ in the case of faulty or corrupted system driver installation. To overcome this situation, one should try re-installing the Ethernet drivers.
Persistence Setup, and Cleaning
Question: My customer received error #210026 (SNTL_CLK_TAMP_FOUND). What can be done?
This error can be encountered under the following scenarios:
| Possible Scenarios | Solution |
|---|---|
| When the system clock is tampered (set back) on a standalone or network system. |
Execute sntl_persistence_reset API to correct the time tampering information. For details on how to call this API, compile and execute, refer the sample available at …\<version>\Samples\C\Src\sntl_lspmgmtclean.c location. |
| When the persistence information is corrupted on a standalone or network system. | |
| When the standalone system is not initialized for handling a time tamper enabled license (commuter, grace, repository, time tamper enabled) and a license is requested by the application. |
Execute sntl_persistence_create API to create the standalone persistence data. For details on how to call this API, compile and execute, refer the sample available at …\<version>\Samples\C\Src\sntl_lspmgmtinit.c location. |
NOTE From RMS 9.6.0 onwards, it is mandatory to initialize time tampering on Linux else the already enabled time tamper licenses (running with RMS 9.5.0 or below) will fail on replacing the existing library files with the new ones.
Question: What should be done if the customer happens to delete the persistence files mistakenly?
Ideally, the Sentinel RMS-created files should not be deleted to ensure smooth access to your licensed applications. However, in case the files are removed mistakenly, the system should be cleared up using the steps described in the section Persistence Data-Dependent License Models.
Question: Are Administrator privileges required to initialize the system using the sntl_persistence_create API?
Yes.
Question: Do I need to initialize the system when providing a normal license over a trial license?
You can skip initializing the system multiple times, if it has already been initialized for one of your applications. However, this is not true across multiple vendors.
Upgrading to v18 Licenses
Question – I am an existing customer using the v8.6.x client components and VLS API. If I upgrade to the RMS v9.2 License Manager for certain reasons and use the v18 licenses, will my setup work?
The License Manager, being backward-compatible, will continue to serve clients of older versions as well. Hence, in this setup, licensing will work seamless as earlier.
Question – I am an existing customer using the v8.6.x client components and VLS API. If I upgrade to v9.2 of the RMS License Manager for certain reasons and use the same older version licenses (older than v18), will my setup work?
Yes, your setup will work. However, you will not be able to leverage asymmetric signing because license versions older than v18 are not digitally signed.
Question - I am writing a new application and want to restrict consumption of already-present licenses in the customer environment. How to do it?
In a new application, consumption of older licenses (v17 and below) can be restricted using the API and attributes in the licensing library. Unified API do not allow using older license by default, while the Traditional API allow it. To override this behaviour, refer to Restricting Consumption of Unsigned Licenses (v17 and Earlier).
Question - Even with the same set of license properties, a v18 license (string) seems longer than a v17 license (string). What could be the reason?
This increase in size—in comparison to the v17 (and earlier) licenses—is due to the support for RSA 2048-signing in v18 (and later) licenses.
